Services by SDLC Phase
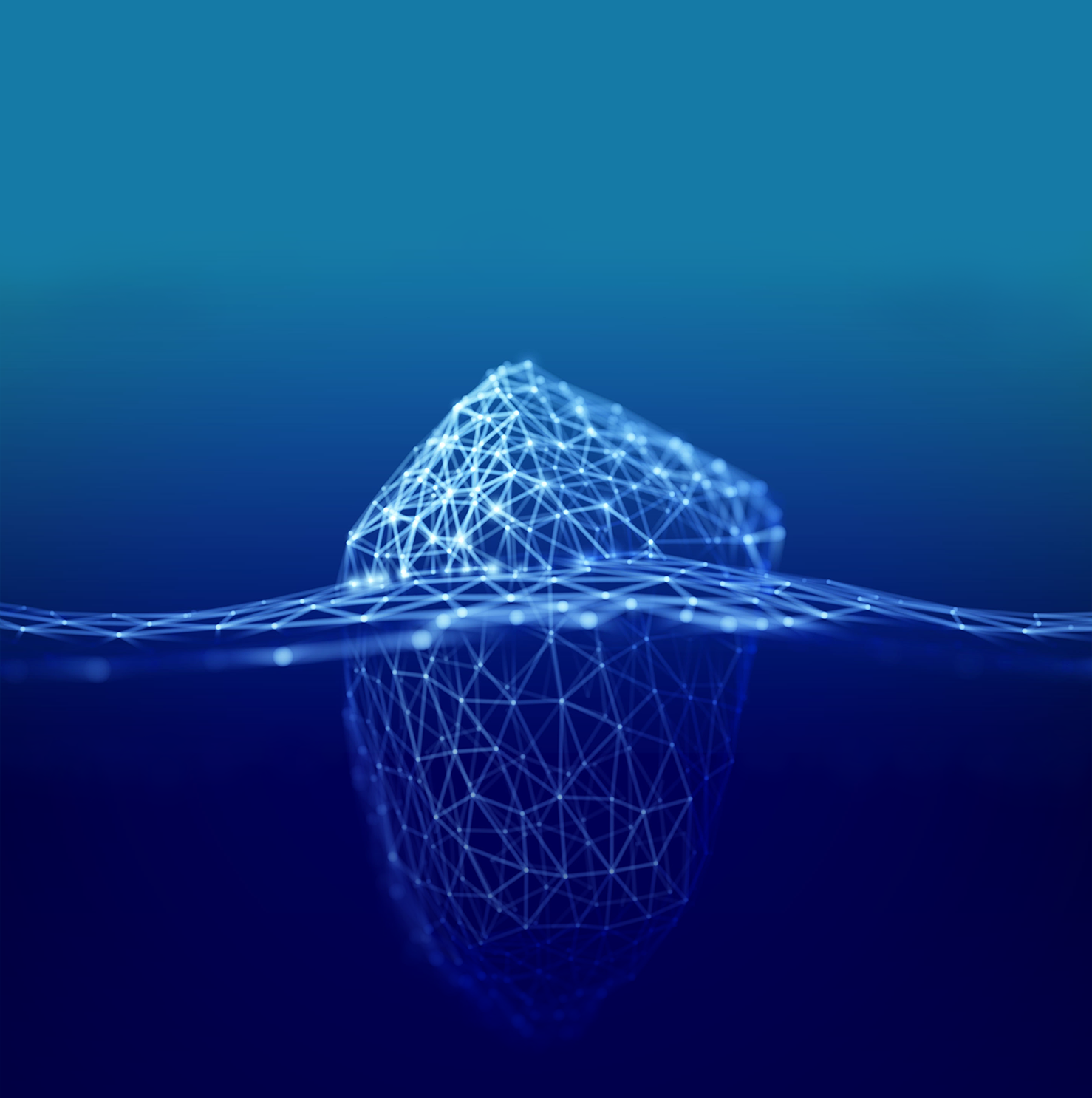
VW’s Pentest Phases
Types of Pentest
Types of Penetrating Testing
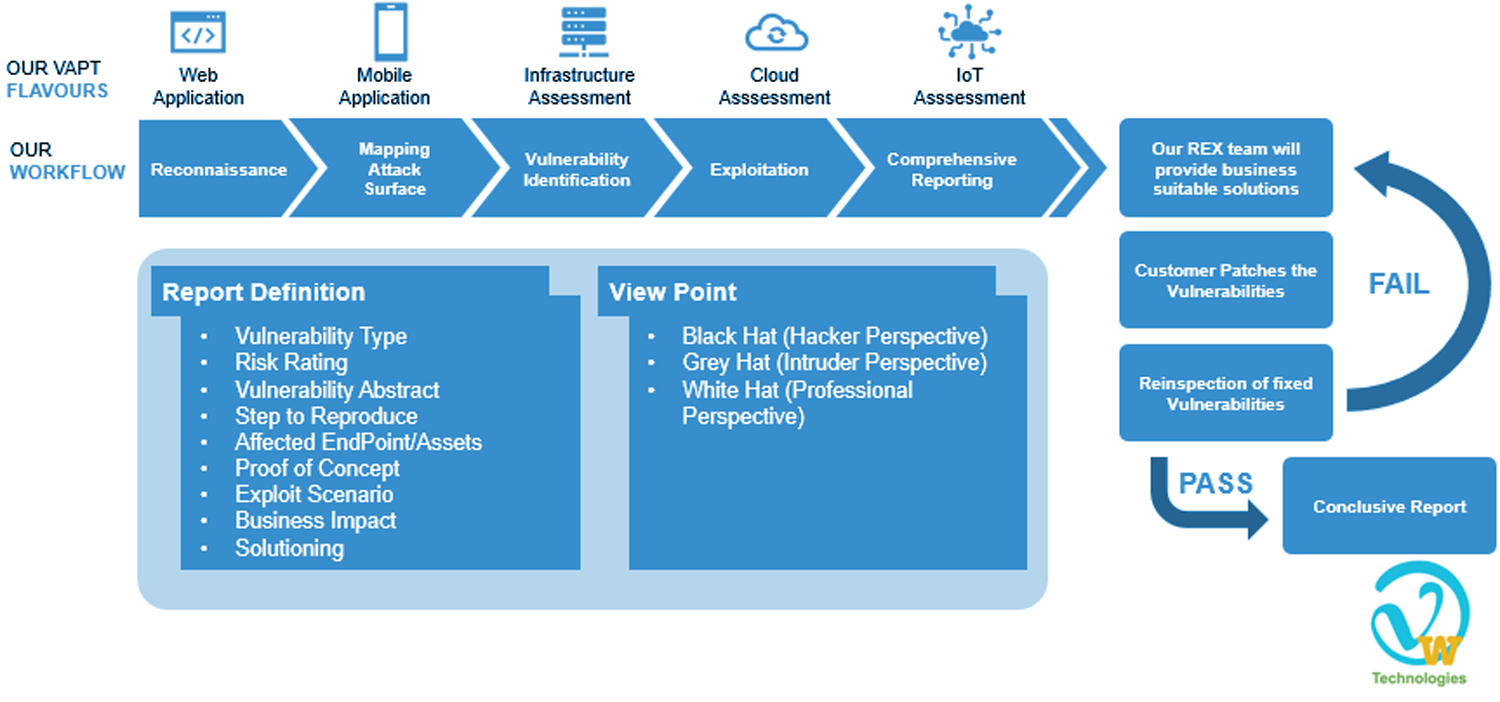
Vulnerability Assessments and Penetration Testing - VAPT Work Flow
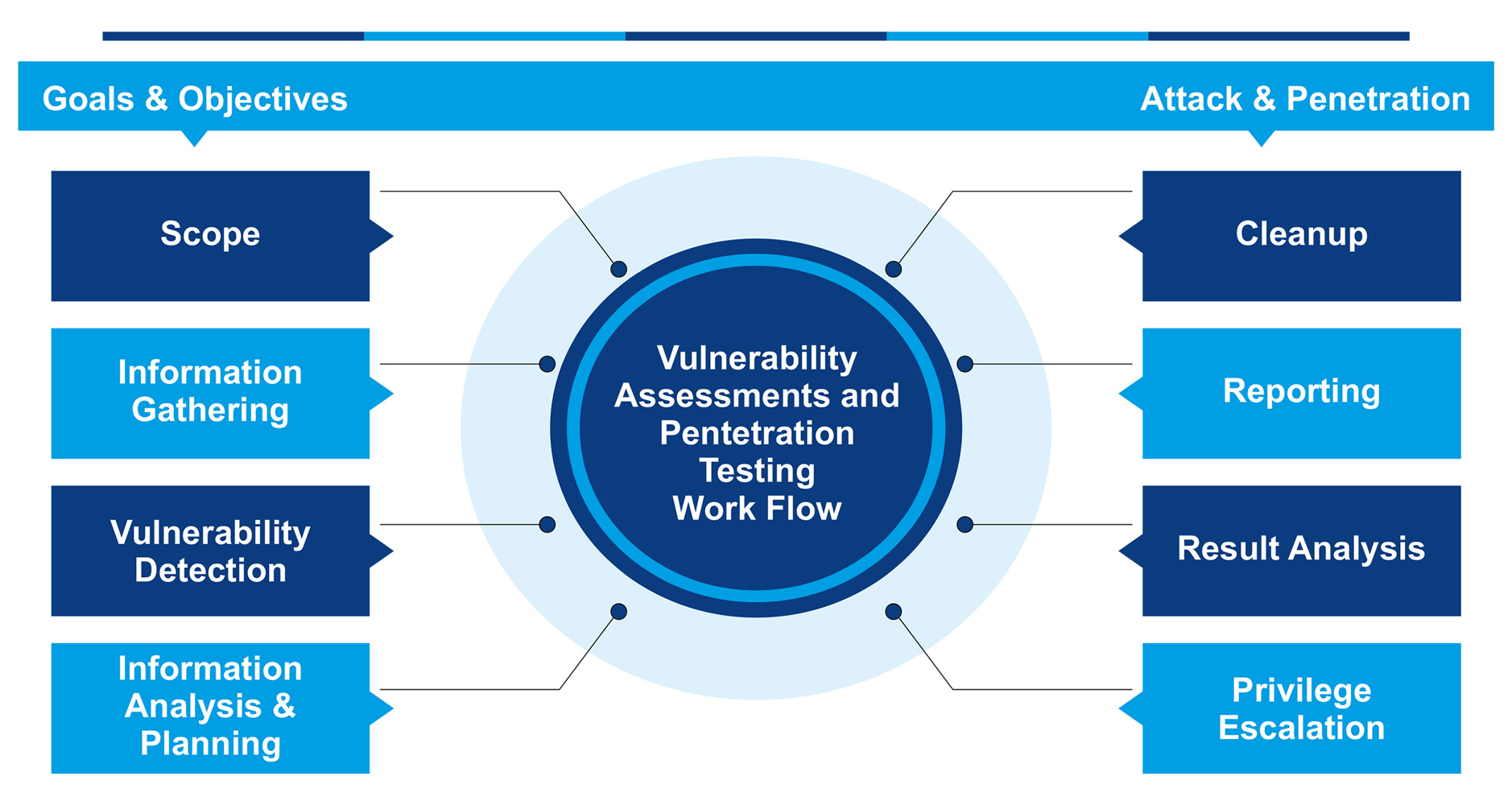
Vulnerability Assessment & Penetration Test
Cloud Security Assessment
- Our Services :
- Cloud Configuration Review
- Cloud Penetration Testing
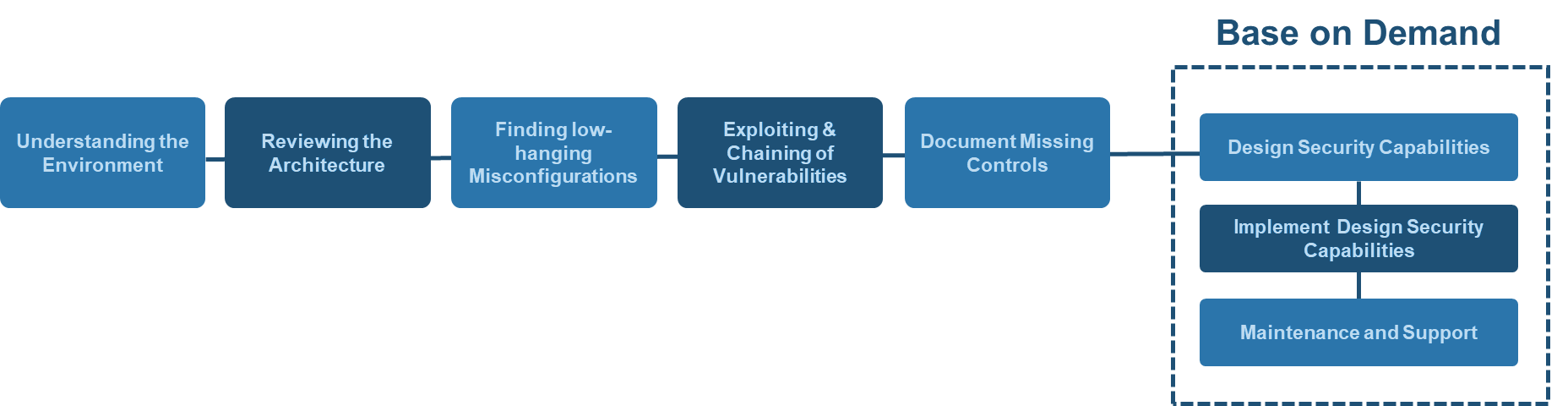
- Clearly understanding the scope and the limits is crucial to gather all the relevant information required to perform the vulnerability scan. The entire architecture is reviewed to find existing vulnerabilities and misconfigurations.
- At VW we combine the results generated from both breadth analysis and depth analysis.
- For breadth analysis, the vulnerability scan is done on the target using the best tools and latest technology. The scan results show the list of vulnerabilities that might be a potential threat to the company and its assets.
- For depth analysis, we will assess known vulnerabilities, security misconfigurations, excessive privileges, SSRF, bypassing existing controls.
- To point out the vulnerabilities that can cause serious damage, the testers then perform penetration testing. After exploitation the tester escalates the privilege and tries to take full command and control of the cloud infrastructure.
- Based on the demand we also design and implement security capabilities. To conclude the security posture of the cloud environment, the results are generated and analyzed. The found vulnerabilities and the precise solutions are presented in an elaborate and eloquent report.
- Maintenance and Support is also a part of our service depending on the customer’s requirement.
IoT Assessment
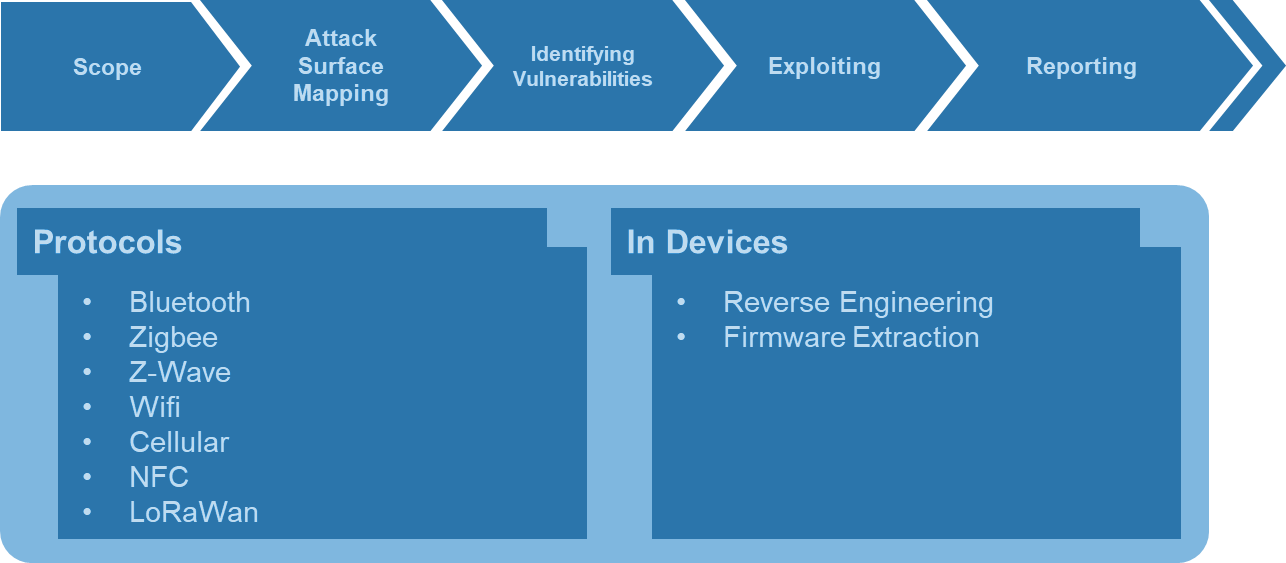
We conduct assessment on all the levels of the IoT architecture
-
Sensor
-
Transmitter
-
Wireless Network
-
Cloud
-
User Application
Assessing the IoT technology end-to-end will help the organizations to balance the risk and threats that keeps varying with market change.
Our methodology
is based on the standard approach of assessing the IoT device.
Syndication & Leads API (Add-On)
-
First, the scope is defined followed by gathering relevant information and mapping the attack surface.
-
The next step is to identify the vulnerabilities and exploiting them from a real-time attack perspective.
-
The found vulnerabilities and exact solutions are presented in an elaborate and eloquent report.
SOC (Security Operation Center)Implementation
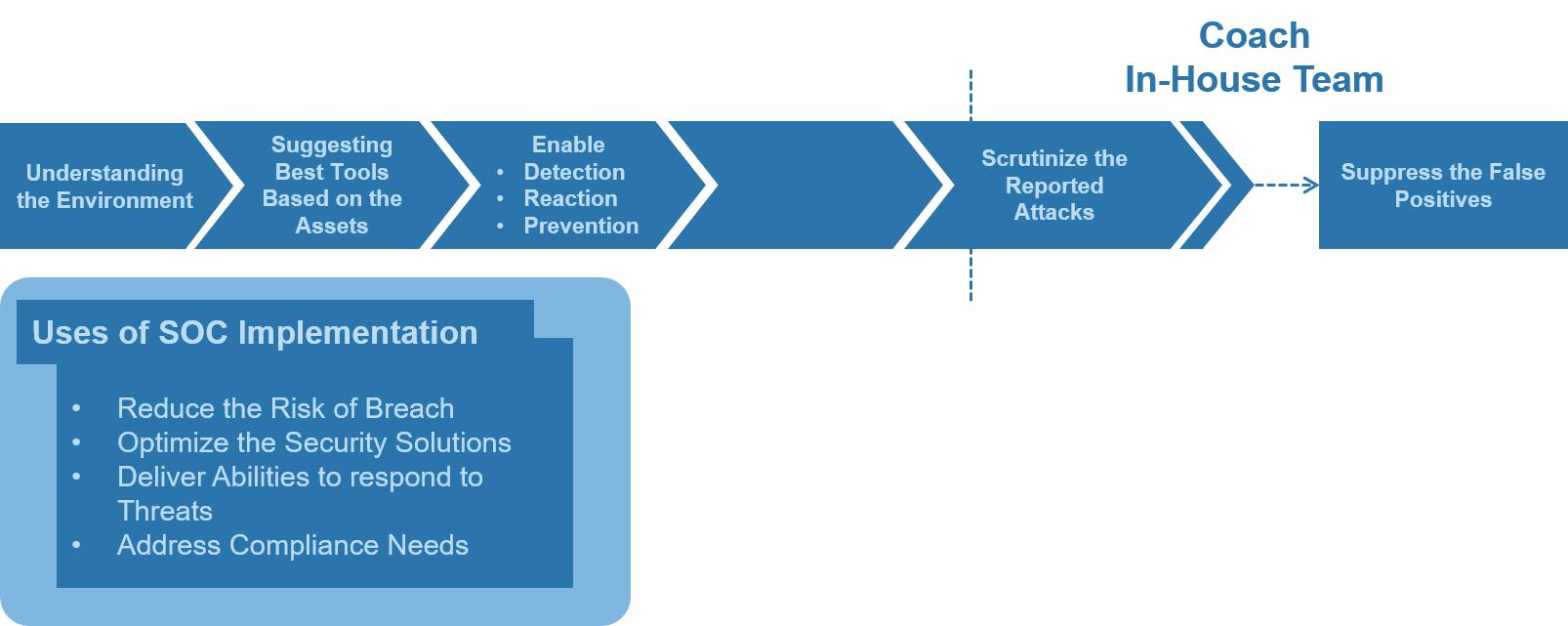
SOC is an essential part of every organization to Detect,React,Prevent cyber risk.
Our SOC implementation services include:
-
Choosing right tools and methodologies as per the customer’s business requirement
-
Enable monitoring, detecting, preventing, responding and reporting capabilities to handle security problems/incidents
-
Through integrations, we can make sure to regularly report/alert the incidents through online dashboards, emails, phone calls etc.
-
Our strategy involves the very basic understanding of the organization's environment. Based on the unique requirements and assets of the company we suggest the best tools available in the market.
-
Our next step is to enable the Detection, Reaction and Prevention process of the SOC implementation. In case of any occurrence of a security incident, our implementation enables the team to react spontaneously and communicate the issue to the respective authorities and employees to contain the issue.
-
We will enable detailed reporting with business suitable solutions to the executives as well as the technical team.
-
We also coach the In-House team based on the existing and past reported attacks.