Compliance and Certifications


Cyber Security Solutions Services
Your Security is our vow, design your business against the latest Cyber Threats with VW Software Technologies.
Iteck Co is the partner of choice for many of the world’s leading
enterprises, SMEs and technology challengers. We help businesses elevate their value
through
custom software development, product design, QA and consultancy
services.


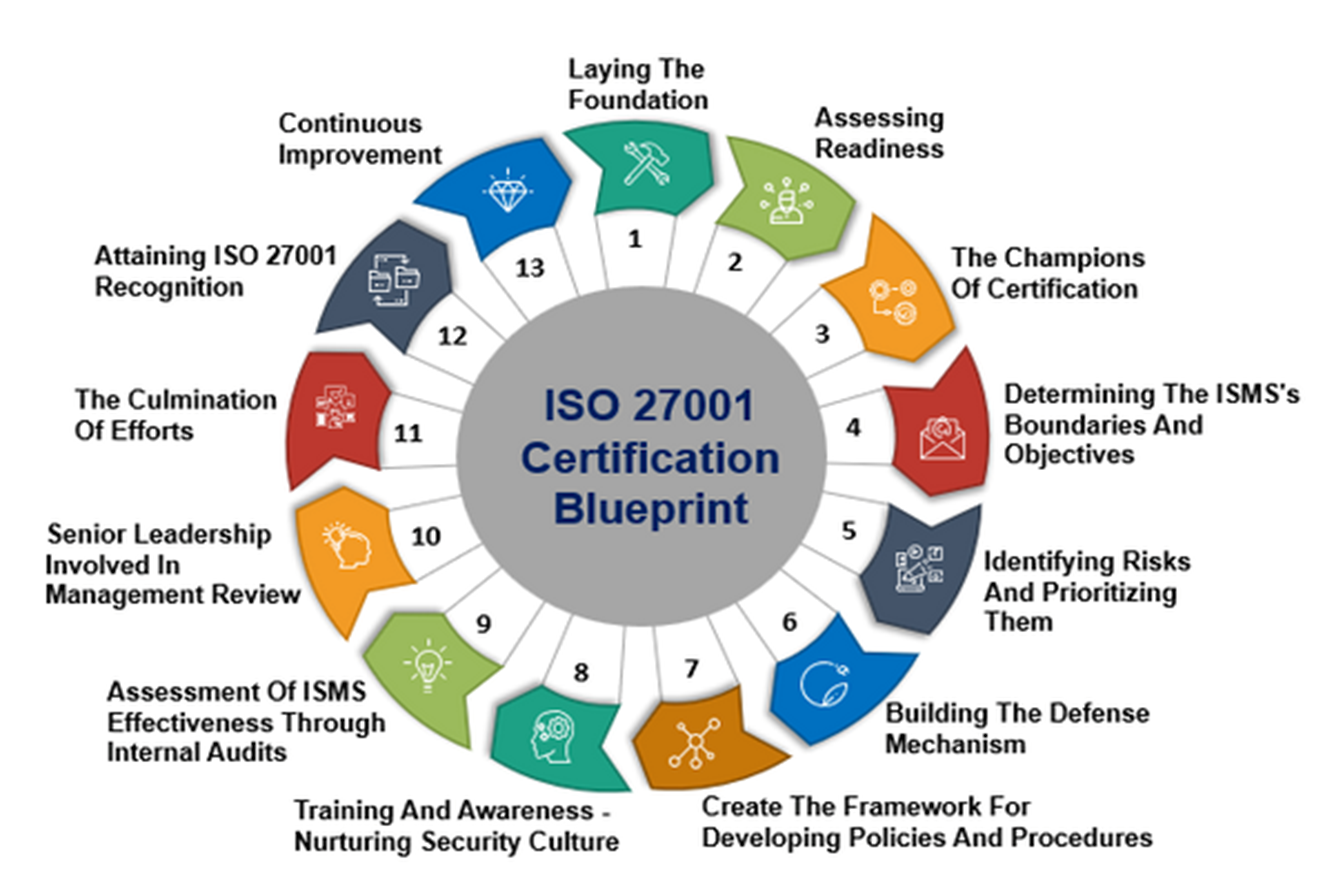
What is internal security audit?
Internal Security Audit is a Process of reviewing the design and implementation of Security Controls for its effectiveness and compliance to Information Security Management System
We begin by defining the scope of the audit and listing down the assets that are crucial to the operations
The second part of the audit is to identify the existing vulnerabilities and threats that can potentially be harmful to the organization
This step is crucial in understanding the existing defense structure of the company and how effective would it be against an attack
Setting a score to the vulnerabilities identified would help you prioritize the threats and act on them according to trends and market scenarios
Documenting this whole process is what is going to help with strategizing the security controls appropriately

Understand the need for Data privacy assessment and evaluate the existing scenario of data management
Define the steps involved in the data processing and elicit them
Consult with our team of expert to carry out data privacy assessment for your organization
Analyzing the necessity and proportionality of the procession techniques
Spotting the risks and chalking out the measures needed to mitigate the risks involved in implementing the control measures

What is data privacy assessment?
Data Privacy Assessment is a process for identifying the risks to data privacy caused by the processing personal data and recommending the ways to manage the Risks. Undertaken primarily for Organization, programs, projects, processes and technology Products.
What is Kubernetes audit?
It is an audit process where the activities generated by application and users who use the Kubernetes API is audited. This procedure documents the audit records chronologically and provides a highly security relevant report.
We begin by defining the scope of the audit and listing down the assets that are crucial to the operations
The second part of the audit is to identify the existing vulnerabilities and threats that can potentially be harmful to the organization
This step is crucial in understanding the existing defense structure of the company and how effective would it be against an attack
Setting a score to the vulnerabilities identified would help you prioritize the threats and act on them according to trends and market scenarios
Documenting this whole process is what is going to help with strategizing the security controls appropriately

